Here is my story about SSL certificates. I have an ongoing project at my workplace and the site is already secured with SSL. And at the end of itsexpiration the site went down. It doesn't feel good as a developer when that happens. This article is hence written to acknowledge my procedures.
Let’s have some basic knowledge first:
HTTPS— Hypertext Transfer Protocol Secure
This communicates securely through the computer network. It can besecured by TLS or SSL. Once you secure the transfer it protects against“man-in-the-middle attacks”. For example, protection from eavesdropping and tampering. All these happen because of the bidirectional encryption of communication between the client and the server.
SSL — Secure Sockets Layer
TLS — Transport Layer Security
Tomake the site secure
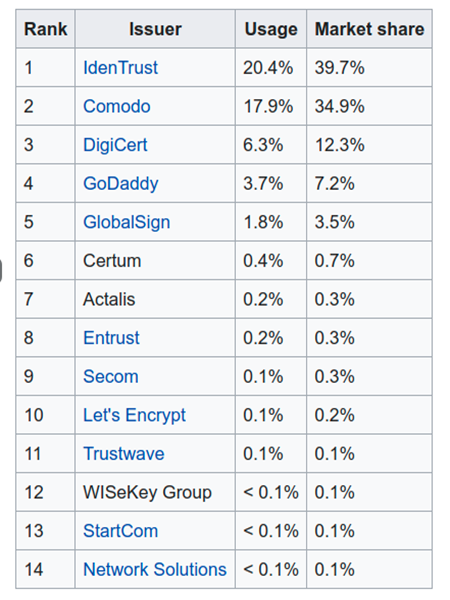
To create a secure connection to the site we need the SSL certificate.This certificate can be generated and obtained by a Certification Authority(CA). There are many Certification authorities available. Most popular agentsare
My story amends with the CA — DigiCert ®
SSLCertificate
This contains a pair of keys.
1. Public Key
2. Private Key
Above keys are used to establish a encrypted connection. Also SSL Certificate will contain your;
3. Domain name
4. Company name
5. Address
6. City
7. State
8. Country
9. Expiration date of the certificate anddetails of the CA
Here are the steps to generate and install the SSL certificate.
This project is done with Ruby on Rails + Nginx, and Ubuntu server.
Step01 — Create a CSR
CSR stands for Certificate Signing Request.
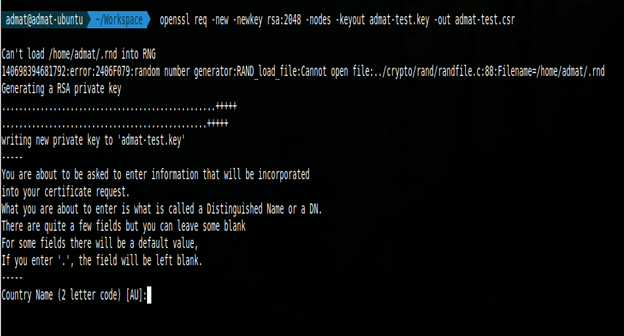
We must create a CSR before ordering a SSL certificate. CSR is anencoded file with the public key and some information that is required to identify the company. To generate the CSR, following would help. (change thetest to your domain name)
open ssl req -new -newkey rsa:2048 -nodes -keyout test-domain.key -outtest-domain.csr
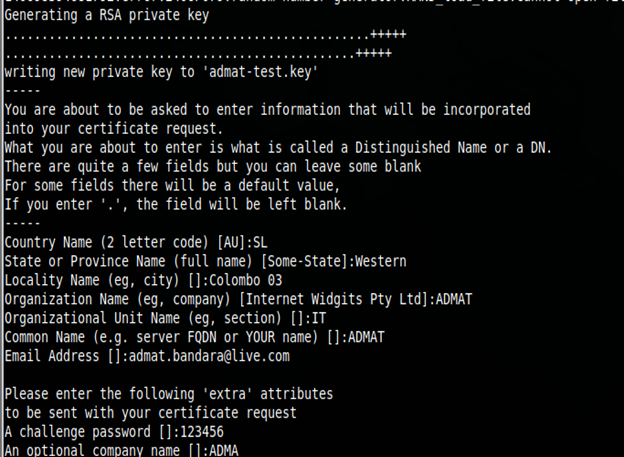
Once this runs, it asked many questions about the organization.
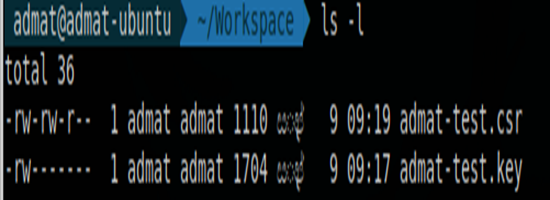
Once it is completed, you can list the CSR and the KEY.
This is how it looks like inside the CSR:
I created a folder named “ssl” in my server. I did this process inside that folder. Now I have both CSR and the server private key.
Step02 — Creating the SSL certificate
The certificate is bought from GeoTrust
The certificate will be sent through an email and it will look
-----BEGIN CERTIFICATE-----
[encodeddata]
------ENDCERTIFICATE-----
According to the certificate chain, Intermediate CA certificate is alsoneeded. It will also look like the above. The intermediate CA certificates canbe found in this link.
Finally, both Intermediate CA certificate and the SSL certificate have to be concatenated. That process can be done simply and the certificate could be seen in a single command.
cat ssl_certificate.crt Intermeidate CA.crt >> domain_name.crt
Now you have the full certificate with you. Let’s move to the next step.
Step03 —Install the certificate into the Nginx
Here is the Nginx Config file of mine.
upstream puma {
serverunix:///shared/tmp/sockets/pml_prod-puma.sock;
}# Forcehttps for http requests
server {
listen 80;
listen [::]:80;
server_name hello.picturemylife.se;
return 301 https://$host$request_uri;
}server{
charset utf-8;listen 443;ssl on;
ssl_certificate/home/deploy/ssl/test-cert.crt;
ssl_certificate_key/home/deploy/ssl/private-key.key;# side note: only use TLS since SSLv2 andSSLv3 have had recent vulnerabilities
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;#listen80 default_server deferred;
server_name hello.example.com;root/home/deploy/pml_prod/current/public;
access_log /log/nginx.access.log;
error_log /log/nginx.error.log info;location^~ /assets/ {
gzip_static on;
expires max;
add_header Cache-Control public;
# Allow CORS
add_header 'Access-Control-Allow-Origin''*';
add_header 'Access-Control-Allow-Methods''GET, POST, OPTIONS';
add_header 'Access-Control-Allow-Headers''Accept,Authorization,Cache-Control,Content-Type,DNT,If-Modified-Since,Keep-Alive,Origin,User-Agent,X-Mx-ReqToken,X-Requested-With';
}try_files $uri/index.html $uri @puma;
location @puma {
proxy_set_header X-Forwarded-For$proxy_add_x_forwarded_for;
proxy_set_header Host $http_host;
proxy_redirect off;proxy_pass http://puma;
}error_page 500 502 503 504 /500.html;
client_max_body_size 10M;
keepalive_timeout 10;
}
Only part necessary for the SSL is
listen 443;
ssl on;
ssl_certificate/home/deploy/ssl/test-cert.crt;
ssl_certificate_key/home/deploy/ssl/private-key.key;
Step04 — Restart the Server Nginx
Nginx has to be restarted.
sudo /etc/init.d/nginx restart
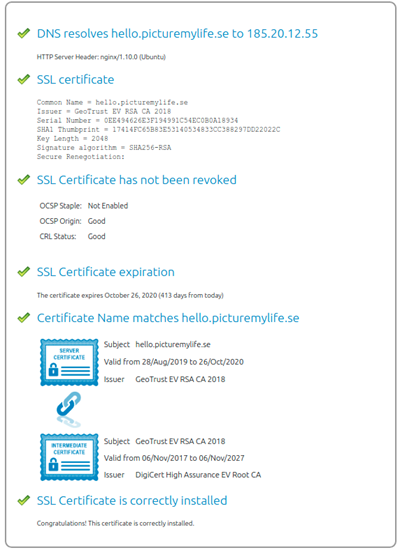
Step05 — Verifying the Security
It is better to verify the security. There is a ssltool provided byDigiCert for verification. This is the link.
Or the following site can be opened with the domain-name as a host inparams.
https://www.digicert.com/help/?host=domain-name
Here is the result of our server domain.
The End.


.png)




